Using Big Data to Defend Against Cyber Threats
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 3236 words | ✅ Published: 18 Aug 2017 |
Abstract
In today’s world, there are petabytes of data being moved by the minute, that data is analyzed and algorithms are developed so companies can critique and improve their services, ultimately increasing their profit, this is called BIG DATA. Majority of the being moved holds critical information such as social security numbers, health information, locations, passwords and more. When data is compromised BILLIONS of dollars are at risk, affecting the company’s integrity and the people who data is stolen livelihood, the security of big data is vital to a company’s present and future success.
Big data is the large volume data which is difficult in processing through traditional method. Security and privacy for big data as well as Big Data management and analytics are important for cyber security. As the field of Cyber Security is increasingly becoming more and more in demand every day, big data is being pushed to the forefront rapidly for big businesses. Big data’s main role is to mine and analyze large sets of data to find behavioral trends and common patterns. From a cyber security perspective, I feel as though big data has ushered in a new wave of possibilities in regards to analytics and provided security solutions to prevent and protect data from future cyber-attacks. I have cyphered through large amounts text in regards to big data’s effectiveness. It is important to understand its effectiveness to better help companies both utilize and protect its data from cyber criminals. The break-out participants pointed out that Big Data analysis for cyber security is for malicious adversary that can launch attacks to avoid being detected. The Privacy preserving biometric authentication must be secured and biometrics represent sensitive information that needs to be strongly protected. Big Data analysis for Preventing cyber-attacks is vital important in security and data management. Enforcing access control policies in big data stores is very important approach to secure the big data.
Keywords: Network Protection, Analytics, and Analysis
- Introduction
Big data is key to the evolution of technology, it is used to improve the services companies provide by developing algorithms through analyzation of each user’s data. An example of big data would be the popular social media application Instagram. Every user has access to an explore page, that explore page is based off the pictures each user likes, comments on or may have in common with a follower. This small action, improves the experience of the user and increases the time the user uses that application, ultimately bringing in more money. Big data is continuing to be used on bigger platforms including financial services, health services, weather, politics, sports, science and research, automobiles, real estate, and now cyber security. An important way to monitor your network is to set up a big data analysis program. Big data analysis is the process of examining large data sets to uncover hidden patterns, unknown correlations, market trends, customer preferences and other useful business information. So with our topic being how big data analytics can prevent cyber-attack, it’s a pretty simple answer that knowing what data is traveling on your network can help prevent a cyber-attack by helping you to track everything that comes onto the network where you can decide if it make be harmful or not. This research will show just how simple it is to recognize unfamiliar data in your network and track where each piece of data goes.
Big data is high-volume, high-velocity and high-variety information assets. Big data are collected through social networking, cell phones, interacting web application. Billions of bytes of data are collected through various medium every minutes. Big data demands cost-effective, innovative forms of information processing for enhanced insight and decision making. There is always issue on the storage and processing these large data set. Storage, management and analysis of large quantities of data also result in security and privacy violations. Privacy and security have compromised while storing, managing and analyzing the large quantities of large data. When dealing with big data, it is necessary to maintain the well balance approach towards regulations and analytics. (http://ceur-ws.org/Vol-1097/STIDS2013_P1_JanssenGrady.pdf)
Data management and analytical techniques can be used to solve security problems. The massive amounts of data are being collected and this data has to be analyzed to defend cyber-attacks. There are issues on security and privacy for big data, data management and analytics to secure the data. Big Data is major in database management. There are many data communities that they are developing large data and its’ solutions for efficiently managing and analyzing large sets of data. Big Data research and development need to do in academic, industrial and government research labs to protect it. Cloud data management include malware detection, insider threat detection, intrusion detection, and spam filtering.
There needs more attention in security and privacy considerations for Big Data including systems, data and networks. Big organization or government agency who are the big data collector need to come together to develop solutions for Big Data security and privacy. The big data privacy, integrity and trust policies need to examine inside the context of Big Data security. The collection and mining data concerning user activities and travel can be used to find out across geographical areas like knowing the originated of the any disease that outbreak. The collection on the social media, posting videos and photos and status can help to recognize to any criminal or terrorist activities. There are many other domains and data technologies play the major role in strengthening security.
The break-out participants pointed out that Big Data analysis for cyber security needs to deal with adaptive, malicious adversary that can potentially launch attacks to avoid being detected. The denial of information attacks is one of the attack that has to be considered as big threat for data privacy. Big data analysis for cyber security need to operate in high volume like data coming from multiple intrusion detection systems and sensors and high noise environments, changing normal system usage data is mixed with stealth advanced persistent threat related data. Big data analytical tools that can integrate data from host, network, social networks, bug reports, mobile devices, and internet of things sensors to detect attacks.
The biometric authentication must be secured. The authentication requires recording biometrics of users and used for matching with templates provided by users at authentication time. Templates of user biometrics represent sensitive information that needs to be strongly protected. In the different environments in which users have to interact with many different service providers have to interact by applying hashing security technique.
Today, cyber threat is increasing because existing security measure systems are not capable of detecting them. Previously, attacks had simpleton aim to attack or destroy the system. However, the destination of Holocene epoch hacking onrush has changed from leaking selective information and demolition of services to attacking large-scale systems such as critical substructure and state authority. Existing defense reaction applied science to detect these tone-beginning are based on pattern matching method acting which are very limited. To defend against these stranger attacks. Researchers can propose a new simulation based on big data analysis technique that can extract information to detect future attacks. This author state “Within the last few 4 sentiency of twelvemonth, Network Behavior Analysis (NBA) has been one of these emerging technologies that have been sell as a security direction tool to improve the current network surety status. The briny focusing of NBA is to proctor inbound and outbound dealings associated with the network to ensure that nothing is getting into the host, package, and application political program systems which helps enhance the overall security measuring section of the network at all story” ( Anand, T). It is stated that approximately 25 % of large endeavor systems will be using NBA by 2011. First, the model has little proactive capableness posture toward preventing any security incident because the architecture is material body with technologies that discover most security events in progression while it misses opportunities to detect and firmness other small menace before it become problems job for the network.
Enforcing access control policies in big data stores is to secure the data storage. Some of the recent Big Data systems allow its users to submit arbitrary jobs using programming languages. This creates challenges to enforce fine grained access control efficiently for different users. To control such challenge there need to apply how to efficiently enforce such policies in recently developed Big Data stores.
Big Data analysis for Preventing Cyber Attacks is vital important in security and data management. Big Data analysis systems that can easily track sensitive data using the capture provenance information can potentially detect sensitive information goes in the hacker’s hand. Building the provenance aware Big data analysis systems is needed for cyberattack prevention. The big data tool is for cyber security can potentially mine useful attacker motivations, technical capabilities, and modus to prevent future attacks.
At the point when managing security issues in the present civil argument encompassing enormous information investigation, the feeling that one may frequently accumulate is that we are within the sight of a contention between positions which can’t without much of a stretch be accommodated. It is as though protection were an obstacle to development spoke to by the open doors offered by big data, a weight originating from the past. Then again as though big data will bring the end of protection, an inescapable infringement of the private circle for mechanical advancement. We tend to be skeptical on this thought of a contention and, rather, we feel this is just history rehashing itself, like each time an innovation move happens, particularly at its initial stage. Toward the end, it is every one of an innocent encounter between the individuals who just observe the rankles and the individuals who just see the advantages. The story however is considerably more perplexing and, over the time, these prerequisites can’t fit in cliché plans. To state it in an unexpected way: big data investigation is digging in for the long haul, and additionally security. The objective of this part is to blueprint how the innovative capacity to remove esteem from information for cutting edge society and the control over it, which is exemplified by security standards, can succeed together.
- Understanding Infrastructure
The more data security experts must analyze, the better they can understand the infrastructure of a complex network. The big network attacks of recent memory are analyzed on a big data scale This shows analyst, how to improve the design of the networks infrastructure and implement security tools to negate cyber-attacks. The more secure and sound the foundation of a network is the less likely data would be compromised.
- Understanding Hackers
Big data is also being used to pinpoint which hacker is guilty of committing the cyber-attack. Security experts can analyze attacks and connect the hacker’s habits or routines when they attack a network. Cyber experts can react quickly and perform efficiently when they’re familiar with a hacker’s routine, possibly tracking the hacker’s actions and possibly finding the location of the hacker. In addition, by using big data, security experts are also able to find hackers through different social media platforms such as, Facebook, Instagram, YouTube, and many other forums that may be a site where other hackers may reside.
Hacking has leaked personal selective information or were done for just fame, but recent hacking targets fellowship, administration agencies. This variety of attempt is commonly called APT (Advanced Persistent Threat). APT attack is a special kind of onslaught that use mixer engineering, zero-Day picture and other techniques to penetrate the target scheme and persistently collect valuable entropy. It can give massive impairment to national agencies or initiative. Another author states “An advanced persistent threat (APT) uses multiple forms to break into a network, avoid detection, and harvest valuable information over the long full term. This info-graphic particular s the attack phases, methods, and need that differentiate APTs from other targeted approach” (Siegel, J. E.). Security system of pattern for spotting and security measure system of rules against cyber-onrush are firewalls, trespass detection arrangement, encroachment bar system, anti -viruses’ answer , data base encryption, DRM solutions etc. Moreover, integrated monitoring technologies for managing system log are used. These security department solutions are developed based on signature. Per various reports, trespass detection systems and intrusion bar systems are not capable of defending against APT onset because there are no signature tune. Therefore, to overcome this issue, security expert is offset to apply data minelaying technologies to detect previously targeted attacks. We propose a new exemplar based on big data analysis technology to prevent and detect previously unknown APT attacks. APT attack is usually done in four steps: intrusion, searching, collection and attack. Figure one describes the attack procedure in detail.
- Development of Security Tools
Hackers can develop complex tools that can find vulnerabilities in a network. By way of big data, cyber experts can develop tools to counter the hacker, aiding security experts in compliance reporting, monitoring, alerting and overall management of complex systems. A big data analytical tool a lot of companies are becoming familiar with is Lumify.
- Lumify
Lumify is an open source tool that creates a visualization platform for analysis of big data, including 2D and 3D graph visualizations, full-text search, complex histograms, interactive geographic maps, and collaborative workspaces.
Search Results
The user can upload their own personal data or begin with a search with a built-in search engine. The search engine can find artifacts such as documents, images, and videos or entities, which are individual terms pulled out of the artifacts by an analyst during the data extraction process.
The data can also be edited to fit a specific search by using Lumify’s built in filters, decreasing the amount of data that is unusable for this specific search (pictured below). After the search results are found the user can use the graphic visualization tool.
Graphic Visualization
Analysis of big data can be complex, terabytes of data is combed through, in attempts to connect a common interest. Lumify makes the process of analyzation easier through graphic visualization. After the search is complete (shown above), the user can place the results on the graph through drag and drop. The user then can click on the results and load all related items or related items of a certain type, creating a relationship between the entities. The relationship between the entities can be created or Lumify can find a common interest.

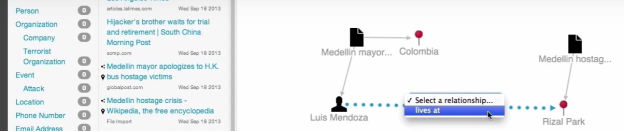
Map Integration
When loading data/entity in Lumify the data/entity can be connected to a geographical location, any entity/data that has a location, the location symbol will be seen next to the entity (pictured below).

In the top left-hand corner of the (pictured below) the user can click the location menu and the global map will appear with the locations associated with the entities that were previously loaded.
The user than can load data within a radius of the entity location and click to see results that relate to the location of your entity.
The map and visual are fully compatible with each other, meaning whatever you do in one area of the database, the other tool is updated with the latest data.

Lumify can be the leading BIG DATA analytical tool on the market because of its ability to display BIG DATA visually.
- Conclusion
The chances of cyber-attacks increase daily because of a dependency on the internet to achieve daily task, per Susan O’Brien of Datameer, 99 percent of computers are vulnerable to attacks, nearly 1 million malware threats are released daily, and the estimated cost of cyber-crimes average a BILLION dollars!! Big data has already produced positive results in its efforts to dwarf cyber threats, per security website HELPNETSECURITY “federal agencies that effectively use big data analytics see improvements in cybersecurity. In fact, 84 percent of big data users say their agency has successfully used big data analytics to thwart a cybersecurity attack and 90 percent have seen a decline in security breaches – malware (50 percent), insider threats (47 percent), and social engineering (46 percent) – because of using big data analytics.” Evolving cyber threats demand a new generation of cyber tactics, big data is leading the way in making the internet and the world a safer place.
We now live in the era of Big Data. Whether we like it or not, companies are regularly collecting reams of information about us as we go about our daily lives. They are tracking us as we visit web sites. They also tracking while we are walking around stores, and as we purchasing products. While some of the information may be mundane, some of it can be highly sensitive, including very specific details about our finances and our health status. To protect the data of our life there always challenging for big organization and government agency.
Big data is high-volume, high-velocity and high-variety information assets and demands cost-effective, innovative forms of information processing for enhanced insight and decision making. Variability is in the data flow’s velocity, which has cost-effectiveness and that leads to the producing of additional processors in cloud systems to handle the load which increases. The log data that are from devices flows into systems, the change and analysis can be done before the curation of data into persistent storage. Volume is the characteristic of the data set and identification of the big data. The cyber must also deal with a richer set of attributes for the resources which adds in a variety of other contextual datasets into the analysis. Variety is the Big Data attribute. This attribute enables most sophisticated cyber analytics. The mechanism is required to bring multiple and highly diverse datasets in scalable way. The security can be obtained through a controlled metadata.
We now live in the era of Big Data, whether we like it or not, companies are regularly collecting reams of information about us as we go about our daily lives, details about our finances and our health status. Ontologies for metadata helps to find out that is already existed, encompassing resources and attack event ontologies. Ontology for metadata is for browsing and querying metadata. The ontology representations of the facts are full confidence in the data being described. While this metadata could be browsed manually, the real value comes if it can be actionable; such that selections over the metadata ontology would automatically construct queries to the Big Data Machine learning technique the best to technique to protect big data. Government also has to take serious action about how the big data have to handle to protect the personal information. So any big data collector or government agency have to take further step to protect the privacy of citizen.
References
O’Brien, S. (2016, May 05). Challenges to Cyber Security & How Big Data Analytics Can Help.
Retrieved October 27, 2016, from
Big Data to Fight Crime. (2015, June 10). Retrieved October 27, 2016, from
https://www.promptcloud.com/big-data-to-fight-cyber-crime/
(2016, August 30). Retrieved October 27, 2016, from
https://www.helpnetsecurity.com/2016/08/30/feds-big-data-analytics-cybersecurity/
Lumify Documentation. (n.d.). Retrieved November 22, 2016, from
Siegel, J. E. (2016). Data proxies, the cognitive layer, and application locality: enablers of cloud-
connected vehicles and next-generation internet of things (Doctoral dissertation, Massachusetts Institute of Technology).
http://csi.utdallas.edu/events/NSF/NSF-workhop-Big-Data-SP-Feb9-2015_FINAL.pdf
http://www.blackhat.com/docs/us-15/materials/us-15-Gaddam-Securing-Your-Big-Data-Environment-wp.pdf
ceur-ws.org/Vol-1097/STIDS2013_P1_JanssenGrady.pdf
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


