Anthem Company Challenges and Risk Assessment
| ✅ Paper Type: Free Essay | ✅ Subject: Business |
| ✅ Wordcount: 3595 words | ✅ Published: 13 Sep 2017 |
Scenario
1. Company Overview
1.1 Introduction
Anthem (formerly WellPoint), via its subsidiaries, offers health coverage to more than 40 million members. Anthem is one of the US’ largest health insurers and is a Blue Cross and Blue Shield Association licensee in 12+ states and operates as Anthem, Empire, and Blue Cross Blue Shield and provides healthcare plans under the guise of Amerigroup, Unicare, and CareMore names in other states. Plans include Preferred Provider Organization, Health Maintenance Organization, indemnity, as well as hybrid plans provided to employers, individuals, and Medicare and Medicaid recipients. Anthem also offers administrative facilities to self-insured groups, as well as specialty insurance.
1.2 Leadership
Anthem, Inc. as an industry leader entices talented and experienced executives to lead corporate decision making, drive innovation and fulfill its purpose of transforming healthcare with innovative products and solutions. The Board of Directors of the organization is headed by Chair Joseph R. Swedish. The shared talents and experience of the Board of Directors aids in guiding the organization as they toil to be America’s prefered health payer. Anthem is carving the path to aid advance the health care system, make it easier for the consumer to access healthcare and use the facilities to improve the health of its customers.
1.3 Operations
Commercial and Specialty Business, Government Business, and Other are the three reportable segments through which the company operates. Managed care services such as claims processing and underwriting, fully insured health products, and specialty products including dental, vision, life, and disability coverage are provided by the Commercial and Specialty Business segment. It accounts for nearly half of Anthem’s of revenues. Medicare and Medicaid services including Medicare Advantage and Part D of Medicare along with National Government Services and services related to BCBS’s Federal Employee Program are a part of their Government Business. Government segment accounted for 52% of Anthem’s revenues in 2015.
Anthem’s specialty products include long-term care, dental, vision, workers’ compensation and group life and disability insurance. Anthem also provides claims processing, fraud prevention, benefits management, and other administrative services for government-run Medicare plans, other insurance firms, and employer groups through many of its subsidiaries. The company provides services to more than 72 million customers.
1.3 Geographic Reach
In spite of its extensions into other business ventures in recent years, Anthem’s Blue-centric expansion efforts in last decades have enabled Blue-branded health plans at the heart of its business. Anthem Blue Cross Blue Shield is the flagship brand under which company operates including plans in Kentucky, Missouri, Wisconsin, and in another place its operate under the name of Blue holdings. Other Blue subsidiaries includes Blue Cross Blue Shield of Georgia, Empire Blue Cross Blue Shield in New York and Anthem Blue Cross in California.
Apart from its Blue subsidiaries, Anthem’s healthcare plans includes its Unicare subsidiary, which enables the organization to sell individual and group health coverage in locations where it’s not a Blue Cross licensee; operating as Unicare across the US. Anthem through its subsidiaries is licensed to conduct operations in all 50 states.
In Florida, Georgia, Iowa, Kansas, Louisiana, Maryland, Nevada, New Jersey, New Mexico, New York, Tennessee, Texas, and Washington, the company operates under its AMERIGROUP subsidiary, providing health plans for public programs. In 20015 Anthem acquires Simply Healthcare, through which it provides managed care services for Medicare and Medicaid beneficiaries in Florida.
1.4 Sales and Marketing
Through a network of autonomous agents and brokers, Anthem markets majority of its products. Except for company’s large, employer-focused products and national account, which are marketed through independent brokers, an in-house sales force, and customer-hired consultants. The company is currently also focusing its efforts on increasing its online sales and promotional interaction with both its consumers and brokers.
Advertising expenses totaled $313.5 million in 2015, versus $337 million in 2014 and $351 million in 2013.
1.5 Financial Performance
Anthem has experienced steady financial growth, including in 2015 when its revenue grew 7% to a total of $79.2 billion. That increase was principally because of growth in the Government Business segment, mainly as a result of its foreray into new markets and the addition of Simply Healthcare along with its operations in Florida. Additionally, membership in existing markets increased, as did policy rates. However, these advances were partially offset by deteriorations in other segments.
Anthem’s net income has also been increasing for years, however in 2015 it experienced a shy less-than-1% dip to $2.56 billion. In 2015 increase in general and administrative expenses on the account of group’s membership growth and benefits expenses decreased the overall profits. Cash flow from operations increased by 22% to $4.1 billion, as a result of an increase in the commercial and private membership.
1.6 Strategy
Anthem plans to expand its operations and reach through acquisitions which includes the pending merger with Cigna, in amalgamation with organic expansion including addition of new members in current markets.
A significant part of Anthem’s growth strategy is covering the Medicare market. Anthem expects more than 1 million Baby Boomers, who will be eligible for Medicare every year between 2011 and 2030 across each of Anthem’s Blue-branded states and it is expanding up its Medicare offerings and growing into new service areas to prepare for the change.
Anthem has made some changes to the way it does business as a means of coping with the Healthcare reform. For instance, it has extended into areas such as online health insurance exchanges and increased its premium rates in selective market segments like individuals and local groups. However it backtracked on growing its retail businesses in early 2014 when it sold 1-800 CONTACTS and its glasses.com after a breif period of 18 months from making the purchase. Analysts and shareholders had been apprehensive about its move into retail from the very beginning. Eyewear firm Luxottica purchased glasses.com and its virtual try-on technology and private equity firm, Thomas H. Lee Partners tbought 1-800 CONTACTS.
1.7 Mergers and Acquisitions
To boost and expand its government business division, Anthem bought Simply Healthcare Holdings in 2015. Simply Healthcare Holdings via its subsidiaries Simply Healthcare Plans and Better Health, offers managed care services for members enrolled in Medicare and Medicaid programs in Florida, a crucial market sector for growth of Anthem. As a result of its acquisition now provides services to over 500,000 Medicare and Medicaid members in Florida.
In 2015, Anthem as a part of an industry shaking move, decided to acquire one of its chief competitor Cigna for $48 billion. The joint venture would have formed a health insurance giant providing its services to over 53 million members and bringing in sales of about $115 billion. Anthem anticipated nearly $2 billion in cost savings and take advantage of new prospects fashioned by the Affordable Care Act
1.8 Competitors
- Aetna Inc.
- CIGNA Corporation
- Harvard Pilgrim Health Care, Inc.
- Health Care Service Corporation, a Mutual Legal Reservel Company
- Medical Mutual of Ohio
- Molina Healthcare, Inc.
- UnitedHealth Group Incorporated
2. Current Scenario – Anthem’s Nightmare
2.1 What did happen?
Mr. Smith and Mr. Jones were the former employee of Anthem Inc. They were not only good friends for ten years in life, but also good partner in their work. When they were working in Anthem. Mr. Smith was the database administrator of the IT department, while Jones worked as a database engineer. Based on the trust of the friendship, Mr. Smith gave out the database administrator’s account name and password to Mr. Jones secretly in order to let him help take some job responsibilities when he was out of his office. In addition, Mr. Smith also gave the highest privilege to Mr. Jones’s account to help him work easily.
On January 28, 2016, Mr. Jones received an email from a software company, which he never heard about it, to recommend him a new anti-virus software product. In this email, there was one word attachment named “software introduction” and one link which allows Mr. Jones download and try the software for free. After Mr. Jones downloaded and read the software introduction, he decided to try it. Without recognizing that it was a phishing email, Mr. Jones clicked the link, downloaded and installed the software. At the same time, a Keylogger malware was installed in Mr. Jones’s computer. Using the Keylogger software, the hackers managed to collect not only the Mr. Jones’ account username and password, but also Mr. Smith’s (the database administrator) account username and password, what would be the genesis of a great events in the history of Anthem health care.
Six months went by without the Anthem administrators realizing that up to 7.8 million customer’s personal identifiable information and sensitive health information was stolen. This heavily influenced the privacy of its customer. Except for stealing data, the hackers also changed the configuration of database, which allows them download a large volume data to a foreign server without warnings in the system. The Hackers also installed some malwares and opened a backdoor to access the database, which put the database in the serious risk of downtime.
2.2 The discovery
As is often the case in such situation, Anthem learned of the data breach from law enforcement agencies. On August 1st, 2016, representatives from U.S. Department of Justice notified Anthem’s management that a large number of stolen patients’ record was selling in the black market and all data seems to come from Anthem, Inc.
2.3 Media Exposure and Influences
News about the massive cyber-attack spread quickly leading to Anthem’s Chief Information Officer’s (CIO) and risk manager resignation. Now since the IT and database at Anthem was under audit and required deep scrutiny, access to some of the infrastructures and databases were limited/denied affecting the availability of the information. Mr. Asha, the new risk manager, being the one who initiated this audit now had the unfortunate responsibility of fixing this enormous problem.
It will take several months to figure out what exactly was the fate of these stolen records. On the black market, stolen patient records could go for up to $50 per record which is now much more than that of credit card information which costs up to $30 per record, since newspapers, magazines, and bloggers feast on this kind of information.
Within a matter of days, news of the Anthem hack filled the headlines of every major newspaper, news station, magazine, blog, and social media site. It didn’t stop there, a class action lawsuit followed alleging that Anthem had failed to conduct due diligence into the vulnerabilities of their security system. This was a terrible time for Anthem.
2.4 what did Anthem do after data breach?
After the breach, Anthem was trying to strengthen their protection of customer information, and they have released a new program called AllClear ID to protect customer identity. Anthem offered AllClear ID to customers first two years for free with AllClear Secure and AllClear Pro service. AllClear Secure service offers identity repair assistance, and some dedicated investigator will work to recover financial losses, to restore your credit and to make sure customer identity is returned to its proper condition. At the meanwhile, AllClear Pro provides additional layers of protection including credit monitoring and a $1 million identity theft insurance policy.
The combination of legal expenses, notification costs and reputational damage from the stolen records led to the express spending of millions of dollars by Anthem executives on unplanned IT system upgrades within a short period of three years.
3. Risk Assessment
Introduction for Team Robinson
3.1 Who are We:/ Who is Team Robinson
Mandiant is an American cybersecurity firm that provides incident response and general security consulting along with incident management products to major global organizations and governments. Mandiant is the creator of OpenIOC, an extensible XML schema for the description of technical characteristics that identify threats, attackers’ methodologies, and evidence of compromise. Team Robinson is a team of consultants at Mandiant, experienced in vulnerability and risk assessment and relevant assessment.
3.2 What do we do?
Anthem Inc., has decided to invest $220 MM in improving its IT security capacities. Team Robinson is hired to conduct vulnerability and risk assessment across the organization using appropriate risk assessment framework/s and provide suggestions to maximize Returns on Security investments for Anthem. Mandiant also provides 24/7 customer support service coupled with the leading forensic professionals and legal personnel for this engagement.
3.3 Team Robinson’s Early Findings
In order to perform the auditing process, we analyzed the document about the whole IT infrastructure and technologies used by the company provided by Mr. Asha and came out the potential risk in Anterm. The details are shown as followed.
3.3.1 Anthem Company Assets
3.3.1.1 Hardware
- PC
- Laptop, tablets, cellphone: personal laptop, tablets, cellphone can also be used in the company and access to the private network of the company
- Server Firewall: there is one firewall between company network and internet.
- No separation between business used Wi-Fi and guest used Wi-Fi
Potential risks:
- There is only one firewall in the company, it is easier for the hackers break into the company.
- Allowing outsiders on the private network could open the company up to hacking and data theft.
- Virus and malware may exist in the personal laptop, tablets, cellphone, which are potential risk for the data breach.
3.3.1.2 Data Center Equipment
All computers and equipment in Anthem’s Data Center should be tracked with up to date information on type, model, purchase date, operating system release level, etc. This includes:
- Mainframes
- Application servers: Dell PowerEdge C6320
- Routers: NETGEAR: Nighthawk AC1900 Dual‑Band
- Switch: Cisco 2960-24
- Firewall: Cisco ASA5500
- Disk and tape drives
- High speed printers: Sharp MX-511N
- Data center equipment (UPS, air conditioning units, etc.)
Technically, Anthem uses TeraData for data warehousing, which is a robust platform that’s able to work with several enterprise applications. TeraData has a number of solid security controls available to customers, such as user-level security controls, role-based support, directory integration, traffic encryption, in addition to auditing and monitoring. [TeraData,2014] Federal regulations require companies handling medical information to encrypt the data, but this control couldn’t help if the hacker gets administrator access to the database. There seems to be no controls over the data transfer as the hacker could download data from database.
3.3.1.3 User Equipment
Technology residing in departments of the company i.e., user equipment such as:
- Desktop PCs: Dell OptiPlex 3030
- Laptops: Dell Inspiron 15 3000
- Zone and desktop printers: HP M477fnw Color LaserJet Pro
- Scanners: HP M477fnw Color LaserJet Pro
- Copiers: HP M477fnw Color LaserJet Pro
3.3.1.4 Software Licenses
All software used on organization’s computers should be used in accordance with the applicable software license. Use of unauthorized or unlicensed software will be regarded as a serious violation of the company policy and will be subject to disciplinary action and any such use is without the consent of the company.
- Operating system
- Windows 7 Linux:
- RedHat 7.0
- Mac OS X
3.3.1.4.2 Software Inventory:
- Microsoft Office 365
- Adobe Acrobat Reader DC
- Web browsers: Internet Explorer and Chrome
- Team Viewer 11, which allow employee control their own PC remotely
- Employees are allowed to download and install any third-party software in their own PC
- Anti-virus software: McAfee antivirus, updated in January, 2014
Potential Risk:
- Malwares and virus may be introduced to the company when employees download and install the software in their PC without control. This may cause the downtime of the system or data breach. (transitive risk)
- Anti-virus software is out of date, which means some virus cannot be detected.
- Employee can use Team Viewer to access the company’s network and download data from their PC, which is a potential risk of data breach.
Continued on next page…
3.3.1.5 IT Staff
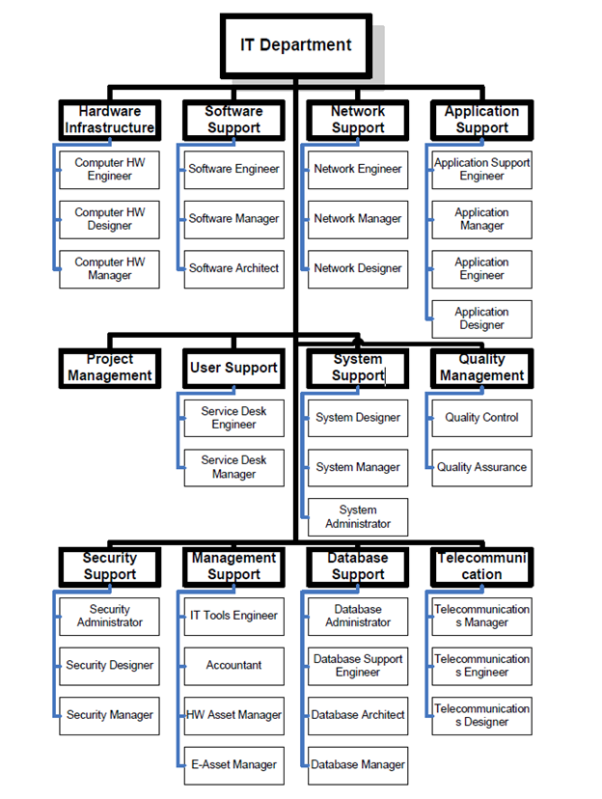
3.3.2Information Security Program:
Anthem must establish and maintain an Information Security Program which must include suitable safeguards, on a risk based matrix for all the resources which includes resources that are owned by company, leased or outsourced.
Information Security Program: The following must be included and documented in the Information Security Program: Annual risk assessment and current inventory of owned or leased electronic devices and critical applications including those containing Confidential Data and metrics, reports, and timelines established by the Office of Information Security.
3.3.2.1Information Technology Security Policy
Policy Number: 898920091132
Policy Date: 01/20/2015
Physical Security
For all servers, mainframes and other network assets, the area must be secured with appropriate ventilation and adequate access through relevant security measures such as keypad pad, lock and scanners etc.
It will be the responsibility of Security Officer to warrant that this requirement always followed. Any company employee who is aware of a breach to this security requirement is obliged to notify Security Officer immediately.
All security and safety of all portable technology, such as laptop, notepads, iPad, mobile phones will be the responsibility of the employee who has been issued with the equipment. Each employee is required to use passwords, pins etc. and to ensure the asset is kept safely always to protect the security of the asset issued to them. In the event of loss or damage, Security Officer will assess the security measures undertaken to determine if the employee will be required to reimburse the business for the loss or damage.
All electric equipment (laptop, tablet etc.) when kept at the office desk is to be secured by password and RSA tools provided by Security Officer.
Information Security
All relevant data to be backed up here – either general such as sensitive, valuable, or critical business data or provide a checklist of all data to be backed up, is to be backed-up. It is the responsibility of Security Manager to ensure that data back-ups are conducted every night and the backed-up data is kept at secure offsite location.
All technology that has internet access must have anti-virus software installed. It is the responsibility of Security Analyst to ensure that anti-virus softwares are installed and confirm that these softwares remain up to date on all technology used by the business. All information used within the business is to adhere to the privacy laws and the business’s confidentiality requirements. Any employee breaching this will be Security Manager.
Technology Access
Every employee in the organization will be issued a unique identification code which they are required to provide to access the business technology. These unique identification code and passwords will be required to reset password for access every 90 days. Each password is to be a 15-digit alpha and numeric character and is not to be shared with any employee within the business.
Security Manager is responsible for the issuing of the identification code and initial password for all employees.
Where an employee forgets the password, or is ‘locked out’ after three consecutive failed attempts, then Security Manager is authorized to reissue a new initial password that will be required to be changed when the employee logs in using the new initial password.
Employees are not authorized to use business computers for personal use.
3.3.2 .2 Information Technology Administration Policy
Policy Number: 898920006209
Policy Date: 01/20/2015
Procedures
All software installed and the license information must be registered on the Central Records Database. It is the responsibility of Security Manager to ensure that this registered is maintained. The register must record the following information:
- What software is installed on every machine
- What licence agreements are in place for each software package
- Renewal dates if applicable.
Security Manager is responsible for the maintenance and management of all service agreements for the business technology. Any service requirements must first be approved by Security Analyst.
System Support Analyst is responsible for maintaining adequate technology spare parts and other requirements including toners, printing paper etc.
A technology audit is to be conducted annually by Security Manager and his team to ensure that all information technology policies are being adhered to.
Any unspecified technology admin requirements should be directed to Security Manager.
3.3.2 .3Anthem’s IT Assets Inventory
|
Asset Type |
Device ID |
MAC Address |
Serial # |
O/S Level |
CPU, Memory, Disk |
Support Vendor |
Model # |
Install Date |
Location |
|
Server |
S1021 |
00-0C-F1-56- 98-AD |
C-5499754 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Server |
S1022 |
02-0C-F1-56- 98-AA |
C-5495625 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Server |
S1023 |
04-0C-F1-56- 98-AB |
C-5499931 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Server |
S1024 |
00-0F-F1-56- 98-AD |
C-5704893 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Server |
S1025 |
12-0C-XX-56- 98-AD |
C-5704891 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Server |
S1027 |
07-0C-F1-S7- 98-AD |
C-5704892 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Server |
S1029 |
47-0C-F1-56- H5-AD |
C-5704897 |
W2012 SP2 |
Quad 1.866Ghz, 4GB, 250GB |
Dell |
C6320 |
6/30/2015 |
Datacenter |
|
Router |
R101 |
00-0C-3F-56- 98-CW |
12559A |
IOS 12.2 |
RAM 64 MB |
NETGEAR |
AC1900 |
7/25/2015 |
Datacenter |
|
Router |
R102 |
05-0C-F1-19- 98-AD |
12560A |
IOS 12.2 |
RAM 64 MB |
NETGEAR |
AC1900 |
7/25/2015 |
Main Office |
|
Router |
R102 |
22-5C-F1-56- 98-GD |
12577A |
IOS 12.2 |
RAM 64 MB |
NETGEAR |
AC1900 |
7/25/2015 |
Branch Office |
|
Switch |
SW09 |
08-0C-R7-56- 98-SH |
366051 |
IOS 14.1 |
RAM 16 MB SDRAM |
Cisco |
2960-24 |
7/25/2015 |
Main Office |
|
Switch |
SW07 |
6H-AG-JK-D5- 98-NM |
367002 |
IOS 14.1 |
RAM 16 MB SDRAM |
Cisco |
2960-24 |
7/25/2015 |
Branch Office |
|
Firewall |
FW107 |
0H-AY-F1-56- 98-SH |
995656 |
IOS 15.5 |
1.5 GB |
Cisco |
ASA5500 |
7/25/2015 |
Datacenter |
|
Firewall |
FW109 |
00-K9-FA-65- 98-H4 |
996554 |
IOS 15.5 |
1.5 GB |
Cisco |
ASA5500 |
7/25/2015 |
Main Office |
|
Firewall |
FW101 |
04-AG-F6-56- 98-SR |
982110 |
IOS 15.5 |
1.5 GB |
Cisco |
ASA5500 |
6/30/2014 |
Branch Office |
|
Laptop |
LT500 |
50-C3-F1-56- 98-A9 |
AF6990577 |
Windows 7 |
Intel Cel 2.86Ghz, 1GB, 60GB |
Dell |
15-3000 |
7/25/2015 |
Main Office |
|
Laptop |
LT501 |
ND-0C-D2-5698-A9 |
AF6950018 |
Windows 7 |
Intel Cel 2.86Ghz, 1GB, 60GB |
Dell |
15-3000 |
07/10/2015 |
Main Office |
|
Laptop |
LT501 |
01-CF-17-59- 98-AS |
AF5520312 |
Windows 7 |
Intel Cel 2.86Ghz, 1GB, 60GB |
Dell |
15-3000 |
07/15/2015 |
Branch Office |
|
Laptop |
LT503 |
4D-02-H1-25- 93-AM |
AF6500900 |
Windows 7 |
Intel Cel 2.86Ghz, 1GB, 60GB |
Dell |
15-3000 |
07/15/2015 |
Branch Office |
|
Desktop |
DT700 |
F2-0D-81-6898-A8 |
DR270051 |
Windows 7 |
Intel 2.86Ghz, 2GB, 120GB |
Dell |
3030 |
07/10/2015 |
Main Office |
|
Desktop |
DT705 |
00-5T-F1-56- 98-ZZ |
DR265510 |
Windows 7 |
Intel 2.86Ghz, 2GB, 120GB |
Dell |
5800 |
07/15/2015 |
Branch Office |
|
Desktop |
DT706 |
04-ZC-F1-Z |
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal


