Survey on Block Chains Technology
Abstract
Block chains is a newly set-up concept which is becoming more and more popular in the last years. Block chains has the permission to save information in an irrevocable as well as tamper-resistant manner by reverting to cryptographic as well as distributed computing. Keeping track of the ownership of tangible and intangible assets is the main purpose. The most widely known use of block chains is bitcoin which attracts more and more people concentrate on the technology of block chains. In this paper, I will introduce block chains technology and apply the concepts to different domains. Different approaches to block chains will be analysed and the progress of current development besides bitcoin is going to be summarized. Although block chains brought us huge convenience and profit in aspects of life, some experts are worried about the safety of block chains. We will also discuss it in this paper.
Keywords Block chains, distributed computing, cryptographic, decentralized, permissionless, permissioned
Recently, World Blockchain Conference was held by World Blockchain Council in Beijing, China on April 3rd, 2018. People come all over the world introduced block chain technology to audiences who may never hear about it before and those experts on block chain discuss the current and future development on the block chain. They also mentioned the topic of safety which many people question a lot including safety for people do trade something of value through the network.
- What is block chains
A block chain which is also called block chain originally, is a continuously growing list of records, which is also known as blocks, secured and linked using cryptograph [1]. Typically, each block will contain a cryptographic hash of the previous bock, a timestamp as well as transaction data [2]. A block chain is inherently resistant to modification of the data by design. Overall, we can consider as an open and distributed ledger which can record transactions between two parties with high efficiency and in a verifiable and permanent way [3]. As we can see, a peer-to-peer network manage a block chain collectively adhering to a protocol for inter-node communication as well as validating new blocks for use as a distributed ledger. If it is recorded, the data in any given block will not be altered retroactively if there is no alteration of all subsequent blocks that requires collusion of the network majority. A block is the ‘current’ part of a block chain and it records some or all the recent transactions. If it is completed, a block will go into the block chain as a permanent database. Every time a block gets completed, it will generate a new one. In the block chain, there are countless number of such blocks. They are all connected to each other like links in a chian in proper linear, chronological order. Each block will contain a hash of the previous block. For the whole block chian, it has complete information about different user addresses and their balances right from the genesis block to the most recently completed block [2]. Figure 1 shows the formation of the block chain. The main chian are the black ones consisting of the longest series of blocks from the genesis block which is in green to the current block. The purple blocks are orphan bocks which are outside the main chain.
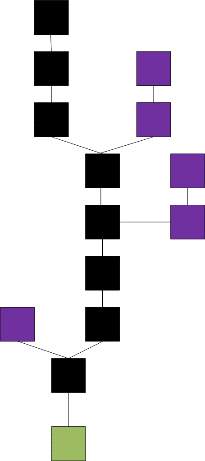
Figure 1. Block chain formation
Byzantine fault tolerance [4] is used during designing and exemplifying the distributed computing so that we can make sure block chains are secured. Therefore we are able to achieve a decentralized consensus with a block chain [5]. It makes block chain greatly for medical records and records management activities including transaction processing and identity managing [6]. Figure 2 shows the basics of block chain.
- History of block chains
In October 2008, in a message which was sent to a cryptography-focused mailing list, it said that Satoshi Nakamoto who is the mysterious creator of Bitcoin had been working on a new electronic cash system that was fully peer-to-peer without trusted third party [7]. In the message, there was a nine-page paper stating a technology which some of them are already been convinced will disrupt the financial system. With the introduction of bitcoin, the cryptocurrency era was born. Block chain, which is the technology behind bitcoin, did not arise out the blue because its origin is shadowy. He used established cryptography tools as well as the computer methods studied for decades to set up a public network of people using it who do not need to trust each other to agree, that a shared accounting ledger reflects the truth. This makes it impossible for people to use one bitcoin twice and solves the problem which had hindered previous attempts to create digital cash [7]. Furthermore, it reduces the need for a central authority to mediate electronic exchange of the currency.
The bitcoin became popular in 2011 and technologists realized that block chains can use to track things more than money. Vitalik Buterin, a 19 years old young man, proposed Ethereum which could record the status of computer programs which are called smart contracts. Coming to 2015, Ethereum which is now a host of competitors and imitators, promises to make a new generation of application like the web apps we are using today, while is powered by decentralized cryptocurrency networks instead of a company’s server [8].

Figure 2. Block chain basic
- Structure
As we mentioned previously, a block chain is s decentralized, distributed and public digital ledger used to record transactions through many computers. In this way, the record cannot be altered retroactively without the alteration of all subsequent blocks and the collusion of the network [9]. A peer-to-peer network and a distributed timestamping server manage the block chain database autonomously. Mass collaboration that are powered by collective self-interests authenticate the network and the server [10]. As the result, it is a robust workflow and participants; uncertainty regarding data security is marginal. We use block chain to remove the characteristic of infinite reproducibility from a digital asset. In this way, it solves the problem of double spending which confused scientists for a long time and it makes sure that the unit of value was transferred only once. So people describe block chain as a value-exchange protocol [11]. Compared to traditional systems, the block chain based exchange of value can be completed more quickly, safely and cheaply. A block chain can assign title rights because it provides a record which compels offer and acceptance. There are three structures which are block, decentralization and openness.
- Blocks
The chain is formed by linked blocks which hole batches of valid transactions that are hashed and encoded into a Merkle tree. The iterative process confirms the integrity of the previous block all the way back to the original genesis block [12].
Separate blocks could be produced concurrently then creating a temporary fork. Any block chain has a specified algorithm to score different versions of the history so that one with a higher value can be selected over others in addition to a secure hash-based history. Those that are not selected for inclusion in the chain are called orphan blocks [12]. It is a name which can be easily understood. The highest scoring version of the database know to peers will be kept. No matter when a peer receives a higher-scoring version, they will extend an overwrite their own database and retransmit the improvement to peers. It is not guaranteed that any entry will remain in the best version of the history forever for the reason that block chains are typically built to add the score of new blocks onto old blocks. There are also incentives to work only on extending with new blocks rather than overwriting old blocks. So the possibility of an entry becoming superseded will go down exponentially [13] because more and more blocks will be built on it.
Get Help With Your Assignment
If you need assistance with writing your assignment, our professional assignment writing service is here to help!
There is another concept called block time which is the average time it takes for the network to generate one extra block in the block chain [14]. Some block chains will create a new block in every 5 seconds [15]. The included data will become verifiable by the time of block completion. This is when the money transaction takes place in cryptocurrency. The shorter time, the faster transaction it will be. For Ethereum, the block time is set between 14 and 15 seconds. While it is 10 minutes for bitcoin.
- Decentralization
The block chain eliminates many risks that come with data being held centrally by storing data across its peer-to-peer network [16]. The decentralized block chain may use ad-hoc message passing and distributed networking.
Lacking centralized points of vulnerability which computer crackers can exploit is one of features of peer-to-peer block chain. Similarly, it has no central point of failure. A public key which is a long, random-looking string of numbers is an address on the block chain. Value tokens sent across the network are recorded as belonging to that address. A private key is like a password which gives its owner access to their digital assets or the means to otherwise interact with the various capabilities that block chains now support. We consider the data stored on the block chain incorruptible. Methods such as the use of public-key cryptography is considered to be the block chain security method [17].
Information and data manipulation are possible when centralized data is more easily controlled. Public block chains make block-level data transparent to everyone evolved by decentralizing data on an accessible ledger [18].
Each node in a decentralized system will have a cop y of the block chain. Database replication and computational trust maintain the data quality [19].
There is not centralized official copy existing and no user is trusted more than others. We use software to broadcast transactions. Messages are delivered on a best-effort basis. Mining nodes validate transactions and add them to the block they are building. Then it broadcasts the completed block to other nodes [20]. Block chains will use many time-stamping schemes, such as proof-of-work to serialize change [21]. Growth of a decentralized block chian is accompanied by the risk of node centralization because the computer resources required to process larger resources required to process larger amounts of data become more expensive [22].
- Openness
Open block chains are more user-friendly than some traditional ownership records which still require physical access to view to the public. At first, all the block chains were permissionless, controversy has arisen over the block chain definition. Here comes one question that whether a private system with verifiers tasked and authorized by a central authority should be considered as a block chain [23]. Proponents of permissioned or private chains argue that the term “block chain” main be applied to any data structure which batches data into time-stamped blocks. Block chains prevent two transactions from spending the same single output in a block chain just as MVCC prevents two transactions form concurrently modifying a single object in a database [24]. Opponents say that permissioned systems resemble traditional corporate database, not supporting decentralized data verification, and that such systems are not hardened against operator tampering and revision. Block chain is defined as a distributed ledger or database which is open to anyone.
- Permissionless
For an open, permissionless or public, block chain networks, the biggest advantage is guarding against bad actors is not required and no access control is needed which means applications can be added to the network without the approval or trust of others. They use block chain as a transport layer. For bitcoin and other cryptocurrencies, they secure their block chain requiring new entries to include a proof of work. Bitcoin uses Hashcash puzzles to prolong the block chain which was designed in 1997 by Adam Back.
Financial companies have not yet prioritised decentralized block chains. In 2016, venture capital investment for blockchain-related projects was weakening in the USA but increasing in China. Bitcoin and many other cryptocurrencies use public block chains. As of April 2018, bitcoin has the highest market capitalization [25].
- Permissioned
Permissioned block chain is also considered as private. It uses an access control layer to govern who has access to the network [26]. Validators on private block chain networks are vetted by the network owner in contrast to public block chain networks. They do not rely on anonymous nodes to validate transactions nor do they benefit from the network effect. We can also use hybrid or consortium block chains when we talked about permissioned block chain. More and more companies are using block chain networks with private block chains which is independent of the public system [27].
- Necessary of using Block chains
If multiple mutually mistrusting entities are going to contact and make some change on the system state, and they do not want to rely on an third party online, that is when we are going to use an open or permissioned block chains.
Figure 3 shows decisions on whether to use block chain under different circumstances. We imagine a situation when there are parties writing the state of the system. For example, a writer is corresponding to an entity with write access in a typical database system or to consensus participant in the block chain.
We do not need the database unless there is data needed to be saved. That is the same thing happen to block chain which is considered as a form of database. If there is only one writer, there is no need for block chain to provide other guarantees and a regular database is better. In terms of throughput and latency, traditional database can do a better job. If TTP [28] which is a trusted third party exists, and it is always online, we can use it to do write operations and state transitions can be verified. What if it is offline? We use it as a certificate authority based on a permissioned block chain. Under this circumstances, all the writers know about it. Under the condition of trusting each other, the best way to solve it is to use a database using shared write access. If they do not trust each other, we then use a permissioned block chain. Everyone in the network can access the state of the public permissioned block chain or be restricted under the private permissioned block chain. Take bitcoin for example, writers who do not know each other will use the permissionless block chain.
Table 1 shows the difference between permissionless block chain, permissioned block chain as well as a central database which is traditionally used. We can tell the performance of traditional central database is more efficiency in terms of latency and throughput. The reason is central database do not need to put extra complexity on the mechanism. Visa, as a central database system is able to process more than fifty thousand transactions at most per second. While bitcoin can only process 7 transections. If we do not worry about compromising security, it can process around 66 transactions. So using decentralized system brings us trade off. We need to think about if there is no mutual trust, what is the performance of the system when it faces many writers; under a certain time, how many state upgrades can the system process.
So it is really important to consider which method we are going to use under different circumstances. We need to figure out the advantages and disadvantages of these three kinds of database system so that the efficiency will be improved. We need to do trade off as well to see which aspect we are focusing on.
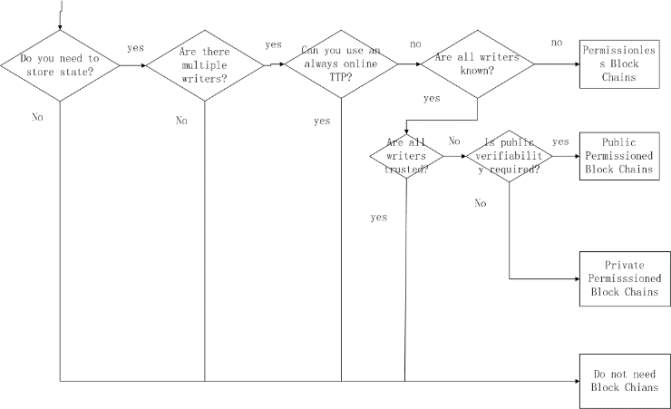
Figure 3. Flow chart on whether to select block chains
| Permission less Block Chain | Permissioned Block Chain | Central Database | ||
| Throughout | Low | High | Very High | |
| Latency | Slow | Medium | Fast | |
| Number of readers | High | High | High | |
| Number of writers | High | Low | High | |
| Number of untrusted writers | High | Low | 0 | |
| Consensus mechanism | Mainly PoW, some PoS | BFT protocols | None | |
| Centrally managed | No | Yes | Yes |
Table 1
- Approaches to block chains
In the following, I will analyse different approaches using block chain technology. Not only bitcoin, but also many other industries could use block chain to improve the efficiency. What would the security and privacy implication be and how a block chain solution might make sense will be evaluated.
- International payments and Interbank
Block chains can be used in many areas such as finance. So I will talk about how people perform international payments as well as interbank in the banking system. There are also solutions which use distributed ledger technology. It is used to simplify and take the place of the system using right now. At last, pros and cons will be discussed using the block chains in the interbank payments.
- Legacy system
We all have experience that it will take two or three days for the bank process the money transfer from one bank to another either using check or debt. If we are using cash, it may be realized immediately.
Let us set a circumstance. If two people are going to transfer money between the same bank, the amount debited from one’s account will be credited into the other’s account immediately. The total amount of the money in the bank will not change and the bank is able to make all these changes in its own book. If the bank accounts are different between two people, the situation will become a little bit complex. If the bank which credits the amount from receiver did not receive the debt from the other bank whose account is the sender, the sum of all debts and credits is not the same. There comes a solution that if two banks’ accounts are linked which is also called Nostro account [29]. When modifying the connected Nostro account, the transaction will be completed at the same time.
In theory, it works. While in the real world, this may bring risk when it leads to large number of debts. As a result, banks will have accounts at a central bank. Those are bookkept in the mirror account which are the accounts mirrored in a local account. They will be used to credit and debit the central bank. If there is an A bank debits Albert’s account, then it will tell the central bank and credits the mirror account. Then the central bank debits A bank’s account as well as credits Ben’s account at B bank whose account receives money from Albert. B bank will credits the mirror account at the central bank and credits Ben’s account. As we can see here, we use the central bank as settlement authorities to distribute the duties from each bank and banks are trusted to fulfil their debts [30].
For now, there are already three banks shown up for a small transfer between two people. More parties may be included. We could batch low value payments and the central bank will not be involved in every payment between banks. If it is an international transfer with the convert of currencies, at this time, there is not any single central bank which could handle the payments. Albert does not have an account with the US central bank.
How to solve this problem? Albert has another bank account at bank C in the US and it is different from Ben’s. We call bank C related bank as A’s. We have to build relationship between bank C and A. The amount of EUR debited in Albert’s account with which US dollars is bought by Albert at bank A. US dollars decrease by 100 and bank A’s ERU increases for the same amount. 100 USD will got to mirror account for bank A’s account at bank C which debits Albert’s amount at its bank and transfer the money to bank B using the US central bank for the settlement. Figure 4 shows the transaction.

Figure 4. Logic flow in international transfer
Thus, if a bank does not have a correspondent bank when transferring in currencies, there may be extra activities that will add delay, complexity as well as high cost. The disadvantages of correspondent banking system are cost caused by the intermediate hops as well as trusts among banks to make sure the system is working.
- Block chain technology for Interbank Payments
For now, in the corresponding banking system, the cost of interbank payment is kind of high and also complex. Central banks including the Bank of Canada and MAD which is known as Monetary Authority of Singapore want to use distributed ledger technology to solve this problem [31]. MAS allow other banks to deposit some money with them and give the same amount of money back on the distributed ledger. In this way, the money will be immediately transferred among the banks on the ledger. This simplify the interbank payments using one simple currency. Although it cannot be used for cross currency transfers, the efficiency is also improved a lot.
At the same time, one of the largest central bank, VISA is working with SWIFT for international payments using block chain technology. The methods based on distributed ledgers which is used to make cross currency payments less complex are developing fast. I think in the near future, they can figure the method out and it will be much more convenient to transfer money especially for students studying abroad.
Find Out How UKEssays.com Can Help You!
Our academic experts are ready and waiting to assist with any writing project you may have. From simple essay plans, through to full dissertations, you can guarantee we have a service perfectly matched to your needs.
View our academic writing services
Ripple which partially replaces the correspondent banking system is trying to provide global settlement network based on a distributed leger [30]. In cases when the foreign currency is low, correspondent banks are still used as the payment process method. Else they will third party liquidity providers providing the required liquidity. If the banks do not trust each other, a payment will require extra hops. Atomic is the biggest feature comparing with the traditional payment method. There are only two situations which are all payments going through or none. While the traditional payments needs the previous payment reverse if there is anything wrong in the middle. XRP will be introduced next as a currency of Ripple used as intermediate currency.
If a party decide to withdraw a deposit, currencies usually have to be trusted to settle the owed debts out of the distributed ledger which are issued by gateways. On the Ripple ledger, XRP allow transactions not entail counterparty risk which means that not all USD are backed by the central bank and have the same issuer. If a USD is on chain, it is not a real USD. In fact, a new parallel currency will be created by every issuer. Ripple will give those relationships which required in the corresponding system to gateways and will not simply remove them.
The currencies which are issued on Ripple will related with real currencies if the system mentioned above use central banks as gateways. The limitation will also be solved. All trust requirements will be removed except the one in the central bank. The reason is that the trust in the central bank is needed in all corresponding currency.
- Perspective
Parties would not like to rely on strong trust assumptions and are risk averse leading block chain technology well suited for financial applications. The interbank payments talked above have multiple parties including banks considered as writers. For a single currency systems, the central bank is the only trusted third party. While, the central bank would like to give licences to banks to participate in the system as a certificate authority instead of verifying every transaction. All the writers in the system are known and we are able to use a permissioned block chain. We can make the block chain private or not. Banks would like to keep their monetary flow private. The trust of the public in the monetary system may be increased if we have public verifiability.
There is a bright future on the development although Ripple have not provided trustless intercurrency money transfers. Central banks are now working on interbank payments as well as with centrally issued on chain currency with block chain technology.
Figure 5 shows a way on how to design block chains for interbank payments. Each of ledgers is a block chain or one currency. If we want to make a payment from A to D, B and C will be used as atomic transaction where they provide currency exchange. We can use techniques used in off-chain payment networks like hashed time lock contracts or by instantiating the block chains as satellite chains. We can use banks to exchange currencies and route international payments when we remove the trust requirements of the corresponding systems in this system.
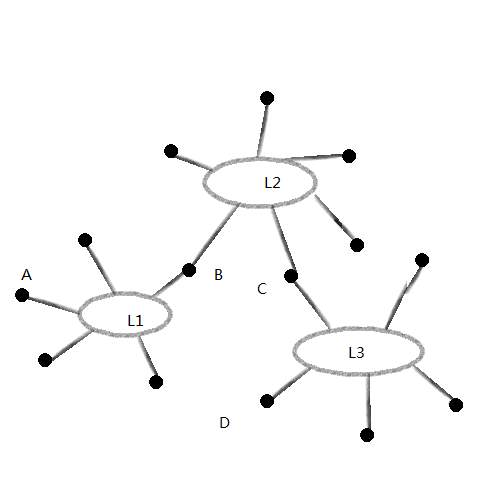
Figure 5 Atomic Currency Payments
- Supply Chain Management
SCM, which is supply chain management is used everywhere in our daily lives. It is a flow of materials and services required in manufacturing given product is managed including many intermediate storage and production cycles until the delivery to the final point of consumption [30]. Many companies contact and trade based on a global scale within a given supply chain. It is really expensive to managing the inventory, detecting processes and failure because of the complexity.
Demand forecasting is becoming difficult because of short product life cycles and long production lead-times. After that, supply chains will face the risk of either excess capacity due to low demand realization or short of product availability. Lack of proper capacity risk sharing will increase the cost of capacity risk in a decentralized supply chain system [32].In order to lower the cost to make the supply chain management solutions work better, companies including Walmart, they want to work out solutions based on block chain. They believe that block chain technology will pave the way to demand instead of supply chains. Companies in various markets can interact with each other and price risks will be balanced.
For the traditional supply chain management, planning and communication will drive it. While in the future, it well be estimated on the past as well as the right now demand. We push information into a stakeholder which hope to get related information to response to errors, delays as well as changes. From this process, companies can decide what product will be in the market and users will drive the demand indirectly.
DCM is known as Demand Chain Management. In this management system, we can tell that the interest of customers will be at the centre of the chain. Companies need to reduce costs, performant customer service and get into the market from idea as soon as possible. By requiring all stakeholders to get a real time visibility of what consumers want and purchase, Demand Chain Management make it possible for this increased flexibility. As a result, all of the demand chains are connected in one network. In order to select optimal production decisions, DCM requires businesses to have a total and accurate view of the whole market. This is different from SCM. SCM may be based on incomplete and inaccurate market assessments and optimizes the flow. In DCM, the stake holders could query the state of the chain management and do not need to wait for a notification. We can say that the information flow in DCM is more pull based than push based.
We all realize that SCM need to be improved and let us see how block chain is used to improve it. We take Skuchain [33] for example. It relies on IBM’s Hyperledger Fabric as its blockchain back end. There could be a wide range of flexibility on how many nodes are actually working in the consensus process in the Fabric’s pluggable consensus options. A single source of truth should be sufficient, because this kind of single trusted database at Skuchain should be able to meet most business need for most SCM.
There is another block chain based solution called provenance [34] if there are more transparency in product supply chains. There will not be any detail on technical support. While it says data cannot be accessed and verified by all actors. Provenance is trying to hide the actor’s identity. While the data would leak a considerable amount of business critical information from different actors such as production volume and times.
Everledger [35] is another company who uses emerging technologies including block chain, smart contracts and machine vision to deduce risk and fraud for banks, insurers and open marketplaces. In order to provide a clear audit trail for stake holders, Everledger records every diamond permanently in the Everledger block chain. Although on their website, they did not provide how they realize their product, they claim that they are using a hybrid model between a private and public block chain to benefit from the permissioned controls in private block chains.
Figure 6 shows the difference between traditional SCM and block chain powered SCM. There are no relationships between traditional SCM, while a block chain powered SCM maintains a distributed ledger where participant can update and read the current SCM state.

Figure 6 Traditional and block chain based SCM
Perspective
Across the SCM, the participants may vary a lot on different supply chains. The same peer may play different roles for different supply chains. The ownership stake of the product will define the segmentation basis for different participants in the supply chain which mean that for every supply chain that a participant is involved in, a single block chain is needed. This will definitely reduce the efficiency.
A SCM needs to save data and different participants of the SCM which own a certain share of the product will be involved in. As we mentioned above, Skuchain needs a single source of trust which removes the decentralized component of the block chain, a trusted central server. SCM will need to use an online TTP. All writers need to know each other which will need us to choose between a permissioned or no block chain.
Here come the question. Need all writers be trusted? SCM has the inherent problem of the interface between the digital and the physical world. A writer will take the control of a human or machine. The supply chain will be compromised as any data could be supplied by a malicious writer if there is no trust between operations of these employees. A block chain will not be needed as a regular database with shared write access could be used if every writer is trusted. The concern might be solved if the connection between the digital and physical world is realized in a secure manner.
- DECENTRALIZED AUTONOMOUS ORGANIZATIONS
DAO which is the Decentralized Autonomous Organizations runs autonomously using a set of smart contracts. Traditional organizations or companies have central control or management. A set of rules which are encoded in smart contracts will define how DAO behaves and evolves. Originally, investors will vote to decide how the funds of DAO should be invested. A permissionless block chain is always a good choice for such designer because the organization is governed in a totally decentralized manner and investors do not know or trust each other as well. So the whole system need to save some state as well as multiple mutually distributing and possibly unknown writers exist.
We can consider decentralized autonomous organizations as a special case. We may use a dedicated permissioned block chain for a single Decentralized Autonomous Organizations. Under most circumstances, DAOs are better to build on top of an existing block chain with an existing currency and do not require its own block chain. Ethereum is an example [8].
- Other areas using block chains
- Trading and Fair Exchange Protocols
People have studied multi-party exchange protocols for a while. Although Bitcoin and Ethereum which are the represents of open and decentralized block chains are so popular recently, people get a chance to design a new type fair exchange protocols using block chain technology. We can exchange digital staffs directly without a trusted third party. It seems that we still need a trusted mediator in case of disputes when we exchange physical things [36].
- Smart contracts
A smart contract is a computer protocol intended to digitally facilitate, verify, or enforce the negotiation or performance of a contract. It allows the performance of credible transactions without third parties. The transactions are also trackable and irreversible [37]. Because the ability being used as a distributed state machine without a trusted third party, block chain can be used in smart contracts. For now, Bitcoin is able to support limited smart contracts. While Ethereum is was the first block chain to support arbitrary code execution on the block chains. It allows all kinds of smart contracts.
If the parties do not want to depend on a trusted third party, block chain will be perfect for smart contracts because they do not trust each other totally. This will make trustless protocols between multiple parties easier. We can use a permissionless or a permissioned block chain depending on the requirements as well as settings.
There are quite a lot we can do in this area because practical smart contracts is kind of new. I am looking forward to see what can be applied.
- Internet of things
It would be really fancy if we apply block chains technology into the Internet of Things which is short for IOT and combine it with smart contracts. In this way, we are able to provide autonomous systems which pay for resources that they consume and get paid for resources that they provide. It is obvious that we can use block chains because the system is decentralized with entities. There is a problem in the supply chain management between the physical and digital world. The values which was read from sensors to the block chains cannot be guaranteed correct. If smart contracts act based on values from the sensor, the sensor and the people who control it have to be trusted. A trusted party can be used instead of block chain if automation is only desired. We need to do some survey on the specific trust assumption and evaluate carefully to see whether the use of block chain will improve the efficiency and bring extra value.
- Proof of ownership
We can use the block chain to proof the ownership of scholar property directly. If the writer or inventor want to make some certifications to prove the ownership, a public block chain could be used as a time stamping service by committing to the digital object with his identity such as a hash as well as publishing that commitment on the block chain. In this way, it could be easily proved when the object was created and it was there since that time. Furthermore, the respective identity was relatively connected. This could provide the evidence of ownership if nobody else can prove the object was published before, while the ownership can not be fully proven. A trusted third party can be used here to provide a proof of ownership such as the office of patent. I think public block chains can do a better job here. It can relief the process to provide a proof in a decentralized way and do not need to reveal any detail information of the digital object.
- E-voting
Voting in physical world seems easy while the cost of it is really high. There comes e-voting. However, there are many problems. Privacy and requiring public certification are two main concerns. For privacy, votes need to be anonymous to prevent coercion. Public certification needs to be provided to prevent the provider of e-voting or people who want to compromise it changing votes at will. The parties evolved in e-voting do not trust each other basically. So people think of basing e-voting system on block chain. It looks like block chains will help to solve those two concerns based on its requirements. There is no solution coming up to be that secure, verifiable and private enough. I hope there will be a solution one day in the future.
- Related work
Because of Bitcoin, there comes the first open and decentralized block chain, launching a large development all over the world. Permissionless block chains such as Ethereum extend the possibilities through more expressive smart contracts as well as improved privacy. Hashed timelock contracts using in the lightning network improve the throughput of block chains and allow transfers of digital assets between different block chains.
Companies such as Hyperledger are building their own permissioned block chains. A predefined set limits the participants here. Permissioned block chains can use more efficient protocols for consensus which is well known such as PBFT [38] for the its simpler than a permissionless block chains.
- Conclusions
In the paper, I briefly talked about how block chains become popular. There are permissioned, permissionless block chains. Sometimes we need to apply specific block chains to the situation. Centralized database has its own advantages as well. Which technological situation is the most suitable depends on which application scenario. We need to consider required trust assumptions, application requirements, throughput and latency as well as involved parties. Block chains technology is widely used in different fields. I introduced the situation block chains technology used in Supply Chain Management, Interbank and International Payments and Decentralized Autonomous Organizations. Block chains has a lot of potential and I think it will contribute more in the future.
References
- Narayanan, Arvind; Bonneau, Joseph; Felten, Edward; Miller, Andrew; Goldfeder, Steven (2016). Bitcoin and cryptocurrency technologies: a comprehensive introduction. Princeton: Princeton University Press
- C. Prableen Bajpai, “Blockchain”, Investopedia, 2018. [Online]. Available: https://www.investopedia.com/terms/b/blockchain.asp. [Accessed: 26 Apr- 2018].
- “The Truth About Blockchain”, Harvard Business Review, 2018. [Online]. Available: https://hbr.org/2017/01/the-truth-about-blockchain. [Accessed: 26- Apr- 2018].
- Y. S. Han, H. T. Pai, R. Zheng and W. H. Mow, “Efficient Exact Regenerating Codes for Byzantine Fault Tolerance in Distributed Networked Storage,” in IEEE Transactions on Communications, vol. 62, no. 2, pp. 385-397, February 2014.
- Raval, Siraj (2016). “What Is a Decentralized Application?”. Decentralized Applications: Harnessing Bitcoin’s Blockchain Technology. O’Reilly Media, Inc. pp. 1–2. ISBN 978-1-4919-2452-5. OCLC 968277125.
- “How Blockchain Fits into the Future of Digital Identity”, American Banker, 2018. [Online]. Available: https://www.americanbanker.com/news/how-blockchain-fits-into-the-future-of-digital-identity.
- M. Editors, “Explainer: What is a blockchain?”, MIT Technology Review, 2018. [Online]. Available: https://www.technologyreview.com/s/610833/explainer-what-is-a-blockchain/.
- D. Vujičić, D. Jagodić and S. Ranđić, “Blockchain technology, bitcoin, and Ethereum: A brief overview,” 2018 17th International Symposium INFOTEH-JAHORINA (INFOTEH), East Sarajevo, Bosnia and Herzegovina, 2018, pp. 1-6.
- S. Armstrong, “Move over Bitcoin, the blockchain is only just getting started”, Wired.co.uk, 2018. [Online]. Available: https://www.wired.co.uk/article/unlock-the-blockchain.
- “Here’s Why Blockchains Will Change the World”, Fortune, 2018. [Online]. Available: http://fortune.com/2016/05/08/why-blockchains-will-change-the-world/.
- A. Illgner, “The blockchain to fix all blockchains”, New Scientist, vol. 236, no. 3153, p. 10, 2017.
- Bhaskar, Nirupama Devi; Chuen, David Lee Kuo (2015). “3 – Bitcoin Mining Technology”. In Cheun, David Lee Kuo. Handbook of Digital Currency: Bitcoin, Innovation, Financial Instruments, and Big DataPaid subscription required. Academic Press. pp. 47–51. ISBN 978-0-12-802117-0.
- A. Antonopoulos, “Bitcoin security model: trust by computation”, O’Reilly Radar, 2018. [Online]. Available: http://radar.oreilly.com/2014/02/bitcoin-security-model-trust-by-computation.html.
- S. Shackelford and S. Myers, “Block-by-Block: Leveraging the Power of Blockchain Technology to Build Trust and Promote Cyber Peace”, SSRN Electronic Journal, 2016.
- R. Yu et al., “Authentication With Block-Chain Algorithm and Text Encryption Protocol in Calculation of Social Network,” in IEEE Access, vol. 5, pp. 24944-24951, 2017.
- Aljosha Judmayer; Nicholas Stifter; Katharina Krombholz; Edgar Weippl; Elisa Bertino; Ravi Sandhu, “Blocks and Chains: Introduction to Bitcoin, Cryptocurrencies, and Their Consensus Mechanisms,” in Blocks and Chains: Introduction to Bitcoin, Cryptocurrencies, and Their Consensus Mechanisms , 1, Morgan & Claypool, 2017, pp.123-
- Brito, J., & Castillo, A. (2013). BITCOIN: A PRIMER FOR POLICYMAKERS. Policy, 29(4), 3-12.
- “How Blockchain Technology Can Change The Way Modern Businesses Work”, Eyerys, 2018. [Online]. Available: https://www.eyerys.com/articles/how-blockchain-technology-can-changes-how-modern-businesses-work.
- Raval, Siraj (2016). “What Is a Decentralized Application?”. Decentralized Applications: Harnessing Bitcoin’s Blockchain Technology. O’Reilly Media, Inc. pp. 1–2. ISBN 978-1-4919-2452-5. OCLC 968277125.
- “Mastering Bitcoin”, Web.archive.org, 2018. [Online]. Available: https://web.archive.org/web/20161201131627/http://chimera.labs.oreilly.com/books/1234000001802/ch01.html#sending_receiving.
- “The Mission to Decentralize the Internet | The New Yorker”, Newyorker.com, 2018. [Online]. Available: https://www.newyorker.com/tech/elements/the-mission-to-decentralize-the-internet.
- “Is Bitcoin a Decentralized Currency?”, InfoQ, 2018. [Online]. Available: https://www.infoq.com/articles/is-bitcoin-a-decentralized-currency/.
- C. H. Lee and K. H. Kim, “Implementation of IoT system using block chain with authentication and data protection,” 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 2018, pp. 936-940.
- T. T. K. Hue, T. M. Hoang and S. A. Assad, “Design and implementation of a Chaotic Cipher block chaining mode for image encryption,” 2013 International Conference on Advanced Technologies for Communications (ATC 2013), Ho Chi Minh City, 2013, pp. 185-190.
- B. Enterprise and J. Ovenden, “Blockchain Top Trends In 2017 | Articles | Big Data”, Channels.theinnovationenterprise.com, 2018. [Online]. Available: https://channels.theinnovationenterprise.com/articles/blockchain-top-trends-in-2017.
- “Blockchain: The Invisible Technology That’s Changing the World”, PCMAG, 2018. [Online]. Available: https://www.pcmag.com/article/351486/blockchain-the-invisible-technology-thats-changing-the-wor.
- N. Popper, “Ethereum, a Virtual Currency, Enables Transactions That Rival Bitcoin’s”, Nytimes.com, 2018. [Online]. Available: https://www.nytimes.com/2016/03/28/business/dealbook/ethereum-a-virtual-currency-enables-transactions-that-rival-bitcoins.html.
- J. Zou, Y. Wang and M. A. Orgun, “A Dispute Arbitration Protocol Based on a Peer-to-Peer Service Contract Management Scheme,” 2016 IEEE International Conference on Web Services (ICWS), San Francisco, CA, 2016, pp. 41-48.
- Q. Liu and K. Li, “Decentration Transaction Method Based on Blockchain Technology,” 2018 International Conference on Intelligent Transportation, Big Data & Smart City (ICITBS), Xiamen, China, 2018, pp. 416-419.
- M. Peck, “Blockchain world – Do you need a blockchain? This chart will tell you if the technology can solve your problem”, IEEE Spectrum, vol. 54, no. 10, pp. 38-60, 2017.
- R. Room, “MAS working with industry to apply Distributed Ledger Technology”, Mas.gov.sg, 2018. [Online]. Available: http://www.mas.gov.sg/News-and-Publications/Media-Releases/2017/MAS-working-with-industry-to-apply-Distributed-Ledger-Technology.aspx.
- M. Nakasumi, “Information Sharing for Supply Chain Management Based on Block Chain Technology,” 2017 IEEE 19th Conference on Business Informatics (CBI), Thessaloniki, 2017, pp. 140-149.
- D. K. Tosh, S. Shetty, X. Liang, C. Kamhoua and L. Njilla, “Consensus protocols for blockchain-based data provenance: Challenges and opportunities,” 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York City, NY, 2017, pp. 469-474.
- “Skuchain: Empower my supply chain | Empower my supply chain”, Skuchain.com, 2018. [Online]. Available: http://www.skuchain.com/.
- “Everledger | A Digital Global Ledger”, Everledger.io, 2018. [Online]. Available: https://www.everledger.io/.
- Aljosha Judmayer; Nicholas Stifter; Katharina Krombholz; Edgar Weippl; Elisa Bertino; Ravi Sandhu, “Blocks and Chains:Introduction to Bitcoin, Cryptocurrencies, and Their Consensus Mechanisms,” in Blocks and Chains:Introduction to Bitcoin, Cryptocurrencies, and Their Consensus Mechanisms , 1, Morgan & Claypool, 2017, pp.123-
- “Smart contract”, En.wikipedia.org, 2018. [Online]. Available: https://en.wikipedia.org/wiki/Smart_contract.
- H. Sukhwani, J. M. Martínez, X. Chang, K. S. Trivedi and A. Rindos, “Performance Modeling of PBFT Consensus Process for Permissioned Blockchain Network (Hyperledger Fabric),” 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS), Hong Kong, 2017, pp. 253-255.
Cite This Work
To export a reference to this article please select a referencing style below:


